'Ransomware in focus' is our new series unravelling the complexities of ransomware groups throughout the ecosystem. By detailing their business strategies, target victims, and the tactics, techniques, and procedures (TTPs) behind their operations, we hope to arm businesses with essential knowledge required to confront and overcome the challenges posed by ransomware. In this edition we focus on an emerging threat: a new operation known as NightSpire.
Background
NightSpire – a potential reference to World of Warcraft lore – is a new extortion group, active in the ransomware ecosystem since early March 2025. Unlike new groups that emerge as a rebrand of an existing and well-established operation, NightSpire individuals appear inexperienced and display a low level of sophistication, suggesting they may be new to extortion operations.
We have identified two individuals using the usernames ‘xdragon128’ and ‘cuteliyuan’ promoting NightSpire’s activities on crime forums on the dark and deep web, indicating their likely affiliation with the group. For example, on 14 March 2025, the individual behind xdragon128 attempted to recruit ransomware affiliates on BreachForums 2 - an English-language forum that banned ransomware-related content and recruitment following a law enforcement takedown in May 2024. This resulted in their permanent ban from the platform.
NightSpire operators also demonstrate a general lack of operational security awareness typical of less experienced actors. This is evident in their use of a Gmail address to communicate with victims, rather than exclusively leveraging a privacy-focused alternative like ProtonMail. A mainstream service leaves a larger digital footprint and is also more susceptible to being shut down by the service provider.
Additionally, an examination of their leak site reveals webpage infrastructure fingerprints (see figure 1 below), providing technical clues that could be traced back to the attackers and used to develop countermeasures such as a targeted takedown.

Figure 1. Server signature line at the bottom of a victim's data posting in NightSpire's leak site, detailing technologies used, including Apache, OpenSSL, and PHP versions.
Moreover, in an incident S-RM recently responded to, we found references to the xdragon128 username in the hostname used by the attackers, 'XDRAGON-SERVER1'.
Affiliations
It is highly likely that NightSpire operators are associated with the Rbfs ransomware group, a little known and low-profile operation. They have shared operators and an overlap in their known victims to date. References to the Rbfs ransomware group have also ceased online as NightSpire has emerged, suggesting this is likely to be a rebrand.
The two known NightSpire affiliates, xdragon128 and cuteliyuan, have both previously promoted Rbfs ransomware online as early as March 2025. On 2 March 2025, xdragon128 advertised victims of Rbfs ransomware attacks on BreachForums 2. A few days later, on March 6, cuteliyuan shared a Telegram link to showcase the group’s victims, although the channel is no longer active.
Further, a review of NightSpire’s leak site reveal at least two victims (see figures 2 and 3) had been previously claimed by Rbfs ransomware (see figure 4 below):
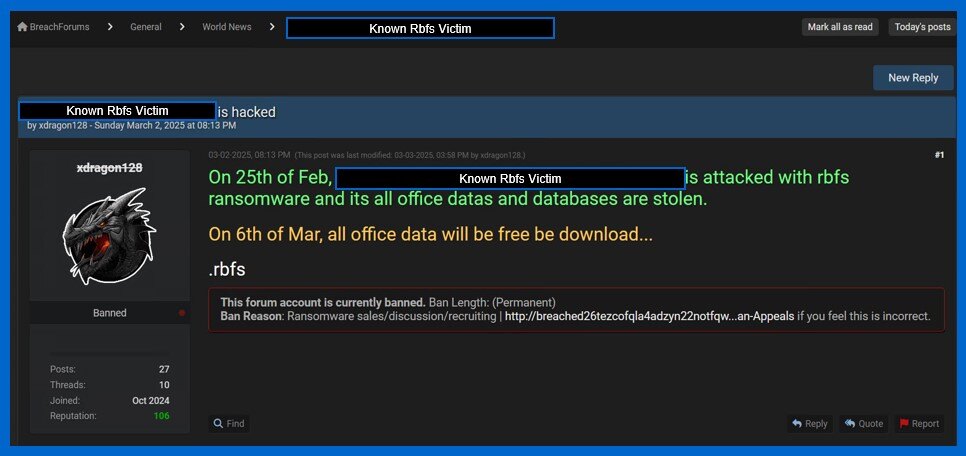
Figure 2. Images of xdragon128’s BreachForums posts advertising Rbfs victims.
 Figure 3. Images of xdragon128’s BreachForums posts advertising Rbfs victims.
Figure 3. Images of xdragon128’s BreachForums posts advertising Rbfs victims.
 Figure 4. Image of NightSpire’s leak site as of March 21, 2025.
Figure 4. Image of NightSpire’s leak site as of March 21, 2025.
Nightspire
Motivations
NightSpire is a financially-motivated group that opportunistically targets all sectors. NightSpire primarily seeks to exfiltrate sensitive information from a target and monetize through extortion or by selling the victim’s data to third parties. More recently, the group has also deployed payloads to encrypt data following exfiltration.
Business model
NightSpire has encrypted victims' data in recent cases, suggesting the group has moved on from a data-extortion-only operation to a more traditional double extortion model. It remains unclear whether NightSpire follows a ransomware-as-a-service (RaaS) model, in which affiliates operate under a profit-sharing structure with operators, or if it functions as a closed group.
Recent activity on BreachForums2 suggests the group's operators are looking to expand their team. On 14 March, xdragon128 advertised an opening for a negotiation specialist for the organization on the crime forum. According to the post, NightSpire would offer the successful candidate 20% of the operation's profits. However, it is unclear if the group is also actively seeking new affiliates to carry out attacks following the model of other RaaS groups.
NightSpire operates a dark web leak site first identified on 12 March 2025, where it has publicized and threatened the release of sensitive data stolen from victims who refuse to pay their extortion demands.
Victimology
Since their emergence in March 2025, NightSpire has claimed at least 11 victims. Although 36% of attacks have targeted the manufacturing sector, it is likely the group targets companies opportunistically across multiple industries. So far, the majority (73%) of NightSpire’s victims have been small to medium-sized businesses, or organizations with fewer than 1,000 employees.
Tactics, Techniques and Procedures (TTPs)
Initial access
NightSpire's known initial access methods include the exploitation of vulnerable external perimeter services such as firewalls and virtual private networks (VPNs). Specifically, the group has exploited CVE-2024-55591, a FortiOS zero-day vulnerability from late last year which allows an unauthorized attacker to gain super-admin access to a Fortigate firewall appliance without supplying valid credentials. Following exploitation of this vulnerability, threat actors can make configuration changes to the device, allowing for connection to and subsequent lateral movement within the victim’s network.
Data exfiltration
NightSpire has used legitimate file transfer tooling such as WinSCP and MEGACmd to perform data exfiltration during their attacks.
Defence evasion
NightSpire leverages a combination of external tools and "living off the land binaries" (LOLBins), including network scanners and FTP clients. This allows threat actors to evade detection by using legitimate tools and processes already present in a victim's environment.
Extortion
NightSpire has promptly posted victims’ names and data on their leak site and have claimed to offer the stolen data for sale to third parties if a ransom is not paid. The group has employed notably aggressive pressure tactics, including issuing payment deadlines as short as two days from the delivery of a ransom note. In at least one case, S-RM identified excerpts from negotiation transcripts published after the victim reportedly failed to comply with demands. During negotiations, the group has been observed employing pressure tactics such as sending emails to employees in pursuit of payment.
Additionally, the group maintains a ‘name and shame’ page titled We say, which highlights non-paying victims. Content on this page has included the victim’s company name, announcements about available stolen data, and, in some cases, free download links. However, the group’s approach to leaking victim data appears to be inconsistent, suggesting a lack of standardized operating practices.
Key takeaways
Unsophisticated threat actors
Inexperienced ransomware groups often behave unpredictably, forcing victims and experienced responders alike to adapt. Unsophisticated attackers may deviate from the expected playbook of more professionalized operations, especially concerning well-established elements of a ransomware negotiation process, such as providing proof of data exfiltration or a working decryptor. Successfully navigating extortion demands from these attackers will require flexibility and balancing well-established tactics with mitigating for the possibility of erratic behavior.
The value of threat intelligence
The use of threat intelligence can be key in identifying indicators of compromise (IOCs) and understanding attacker methodologies and their level of sophistication, allowing for better detection and response. These intelligence-driven IOCs can be integrated into existing security tooling to proactively identify threats, as well as used by security teams once an incident has already occurred to expedite and augment investigation and remediation efforts.
Experience from past groups is valuable when dealing with new threat actors
It is unclear if NightSpire will join the ranks of some of the more prolific ransomware operations and emerge as a long-standing group. However, experience from dealing with past groups remains valuable when encountering emergent threat actors and some of the key technical ransomware mitigations will apply to new and well-established players alike. Conventional advice, such as maintaining secure backups, ensuring timely patch management, and robust endpoint protection, remains critical in prevention and response.
Indicators of compromise
|
Indicator
|
Description
|
SHA256
|
|
MEGAcmd
|
Mega-related tool, used by NightSpire for data transfer as part of data exfiltration.
|
Hash was not retrievable.
|
|
Everything.exe
|
Voidtools’ Everything
Tool filename, used by NightSpire for scanning directories and file enumeration.
|
35cefe4bc4a98ad73dda4444c700aac9
f749efde8f9de6a643a57a5b605bd4e7 |
|
WinSCP-6.3.7-Setup.exe
|
Tool used by NightSpire for data exfiltration activities.
|
Hash was not retrievable.
|
|
7z2408-x64.exe, 7zG.exe, 7z.exe
|
Filenames of 7zip executables, used by NightSpire to compress data prior to exfiltration activities.
|
Hash was not retrievable.
|
|
WINDOWS-DTX-8GB, XDRAGON-SERVER1
|
Hostnames of devices used by NightSpire to conduct their attacks.
|
N/A
|
|
14.139.185[.]60
|
WinSCP remote server IP address associated with NightSpire's infrastructure.
|
N/A
|






