Under Pressure
When an organisation realises it has been hit with a cyber attack, keeping calm under pressure and maintaining clarity of mind can be a lot to expect. More often than not, the instinct is to panic. ‘We got a call on the data breach hotline on a Saturday evening.’ Christine Flammer is a Team Leader for AXA XL’s claims division, specialising in cyber risk insurance. She recounts a standout incident her team has responded to: ‘This one was a ransomware incident where the insured – a first-time victim – unfortunately didn’t contact us immediately. Instead they asked someone in their IT department to research online how to make a Bitcoin payment, made contact with a Bitcoin broker and then sent an executive to meet him at a Starbucks at a roadside pitstop with a bag of cash, about USD 40,000.’
The executive was en route to meet the Bitcoin broker when Flammer’s team received the call and were able to call off the drop. ‘This is exactly the kind of situation we want to avoid with our insured,’ she says. ‘They could have saved themselves hours of research and stress. With just one call to our data breach hotline, we would have connected them right away with our vendors, legal counsel, forensics, ransomware specialists. They would have been in good hands, and much safer for it!’
Erratic behaviour is not unusual for victims of a cyber attack, especially a ransomware attack that can paralyse systems and essentially bring all business to a halt. Under extreme stress, driving to meet a Bitcoin broker on the side of a highway may seem like a rational response. But it clearly isn’t, and one of the key roles the insurance market has come to play in the cyber risk landscape is to prevent just that type of behaviour from taking over when a business falls prey to a cyber attack.
An Evolving Role
The global cyber insurance market had an estimated value of USD 4.3 billion in 2018, and is expected to grow by an annual compound rate of over 25% between 2019 and 2025.[1] This growth is not only testament to increasing awareness about the cyber threat landscape and the business need to transfer some of the associated financial liabilities to third parties. It is also a response to the specialist role several leading insurers have taken on in terms of helping policyholders defend against and respond to cyber incidents. Indeed, a 2017 OECD report on the role of insurance in cyber risk management noted the industry’s potential to improve practices among organisations ‘by promoting risk awareness and encouraging measurement, supporting incident management and providing incentives for risk reduction.’[2] Incident response support, also commonly referred to as post-breach services, has become one of the primary attractions of purchasing a cyber insurance policy. And one of its core attributes is giving targets of a cyber-attack immediate access to the skills and expertise they need to manage the incident in a way that minimises its impact as far as possible.
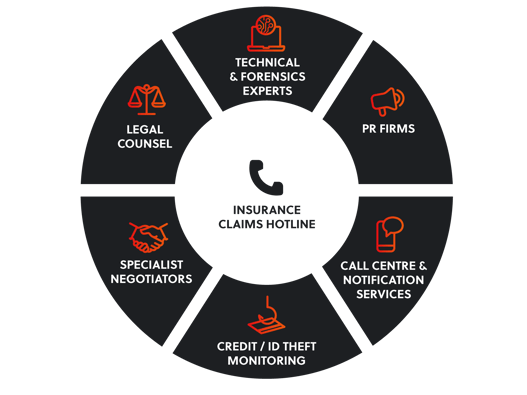
This is especially true for companies who have underdeveloped crisis management procedures, or might otherwise struggle to find the time and resources to establish the network of partnerships required to effectively respond to a cyber incident. Because, while an effective response is inherently team-based, many of the team’s “members” sit outside of the target’s in-house incident response team. From forensics specialists to legal advisors and PR firms, even extortion negotiators – every incident warrants a multi-disciplinary and collaborative response, with a clear allocation of responsibilities. Having this team in place at the point of threat detection will ensure that each threat stream emerging from the root of the attack is dealt with accurately and in a timely fashion.
‘Bottom line is, we are here to help our insured get through a really stressful situation. What that looks like will be different each time, depending on the type of incident that we’re responding to,’ says Flammer. ‘So we leverage our relationships with strategic partners, working with various different types of vendors according to what the situation calls for.’ These relationships include legal counsel, technical experts, PR firms, call centre facilitators and notification vendors, among others, each experienced in responding to the nuances of the attack type in question.
Sample post-breach services
BRINGING THE TEAM TOGETHER
How a cyber incident plays out depends on several interconnected variables and, in almost every case, the potential consequences are multifaceted. A 2019 study of 70 cyber incident-related claims identified ‘63 distinct harms’ emanating from 16 initial cyber attack ‘triggers’. These ‘harms’ ranged in scope from ‘device compromise’ and ‘unavailability of services’ to ‘regulatory violation’, ‘credit monitoring’, ‘reputational damage’ and ‘privacy/breach counselling’.[3] Importantly, the ‘harms’ were deeply interconnected, with one leading to another in an often complex ripple effect that targets would likely find very difficult to predict at the outset. For example, the study found that different incidents, each triggered by stolen credentials, manifested in a variety of distinct ‘harms’, including the payment of fraudulent invoices, the leaking of credit card information, litigation, and malware infections. Each type of event necessitates a structured response that deals with its human, technical, operational, legal, financial and reputational nuances.
Most Common Cyber Incident Triggers
In Flammer’s experience, key to a good response is communication and coordination among the various stakeholders involved. ‘I’ve seen many times where unfortunately, because of organisational changes or lack of incident response planning, the targets of an attack really don’t know who is making the calls,’ she notes. ‘Being able to effectively coordinate within the firm and outside of it is key. Otherwise there’s confusion and time gets wasted, which you simply can’t afford when dealing with the kind of tight deadlines you’re up against in these situations.’
Taking on the role of primary coordinator, the claims team will assemble the most appropriate combination of service providers from a panel of vetted and experienced vendors. They will hold a scoping kick-off call in the first instance, connecting all stakeholders and bringing them up to speed on the situation at hand. From here, the team will determine next steps, allocate responsibilities, and guide the victim of the attack through the response.
Oftentimes, the insured will be meeting its response support team for the first time at this stage. While some vendors will have vast experience working together (for example, legal counsel may bring in their preferred forensics team to operate under legal privilege for the benefit of the policyholder), many of them will be getting to know the target for the first time at a point of extreme stress and time pressure. But this dynamic is changing, slowly. ‘Increasingly companies are beginning to understand that having an incident response plan in place and knowing who the vendors are ahead of time is going to save them time and aggravation once they do have an incident,’ says Flammer. ‘We are seeing more and more insureds, before they have an incident, wanting to be introduced to different vendors. They want to get comfortable with them and really get to know who the people are that they’re going to be dealing with on a daily basis at a time of significant distress and anxiety,’ she notes.
An Effective Response: 'Quick, but Accurate'
Flammer recounts another incident. This time, the target was a small accounting firm and the attack came at the height of tax season. ‘They couldn’t get access to their accounting software, their entire network was shut down,’ she recalls, ‘and this was their livelihood. They really saw this as the end for them.’ However, this time the insured used the hotline immediately, and Flammer was speaking with them within minutes. Her team got counsel on the line shortly thereafter: ‘They were able to pick up the phone and have someone give them the game plan and say alright, this is what we’re going to do.’
How and when an attack is detected depends on the type of attack it is. According to a 2019 study conducted by the Ponemon Institute on behalf of IBM, based on a sample of 500 interviews, the average time from a security incident’s occurrence to its discovery was 206 days.[4] At the point of detection, taking action quickly is important to minimise the impact of the attack by containing the breach, preventing additional compromises and commencing the recovery process as soon as possible.
Incident Detection Time has Remained High since 2015
However, speed isn’t everything. In fact, even in the heat of the moment, patience is key. ‘Having a quick response is obviously very important, but having an accurate response is even more important,’ says Flammer. ‘Getting to the right answers and having the patience and ability to allow the investigation to be completed before running to take action, it’s difficult to do under pressure. Sometimes companies want to go ahead and notify, or tell employees or customers that something occurred immediately,’ she observes. But in her experience, when a response is not accurate, the targeted company risks losing credibility. ‘When you start losing credibility, that’s when we see things really take a turn for the worst,’ she notes, ‘that’s when we often tend to see third-party complaints and regulatory issues arise.’
Accuracy when it comes to incident response requires experience, and many targets of an attack will be experiencing an event of this kind for the first time. ‘Cyber threats keep developing and evolving,’ says Flammer, ‘but a lot of the common pitfalls that we see, those don’t change. How people react to stressful situations, regardless of what the situation is, it tends to elicit the same kind of response.’ When an incident hits, the ability to lean on experience can be the difference between driving along a highway with a bag full of cash and a considered, timely and accurate response. Here, the benefit of having a multidisciplinary response team, who collectively will have dealt with thousands of incidents across multiple sectors and jurisdictions, is invaluable. The likelihood that the target will get through the incident, perhaps battle-weary but far from defeated, grows significantly.
And for Flammer, that’s the part of the job that means the most: ‘It actually feels really good to be able to help companies experiencing a cyber attack,’ she reflects. ‘We see them go from experiencing the ultimate stress level to getting a handle on the incident, going through the steps, and coming out on the other side’.
REFERENCES
[1] Grand View Research (2019). Cyber Insurance Market Size, Share, Industry Growth Report, 2025.
[2] OECD. (2017). Enhancing the Role of Insurance in Cyber Risk Management. Paris: OECD Publishing.
[3] Axon, L., Erola, A., Agrafiotis, I., Goldsmith, M., & Creese, S. (2019). Analysing cyber-insurance claims to design harm-propogation trees. 2019 International Conference on Cyber Situational Awareness, Data Analytics and Assessment. Cyber SA.
[4] Ponemon Institute & IBM Security. (2019). 2019 Cost of a Data Breach Report.




 Email Aaron
Email Aaron





 @SRMInform
@SRMInform
 S-RM
S-RM
 hello@s-rminform.com
hello@s-rminform.com

