The proliferation of defensive tools and rise of Artificial Intelligence has prompted companies to look at high-quality technical solutions for today’s complex security challenges. However, as Melissa DeOrio and Frank de Korte highlight in their article, the importance of people and the power of threat intelligence is a combination that can still outpace even the best technology.
This article is the second in a special series on Cyber Incident Response culminating in an S-RM IR Bulletin in January 2024. Missed last week's instalment? Read Evidence matters in incident response: how S-RM's cyber team use their Wiskess now.
The foothold
Earlier this year, S-RM was called in to support a large manufacturing company who, on first appearances, seemed to have thwarted a cybercriminal’s attempt to steal their data. An unidentified threat actor had, over the course of several weeks, unsuccessfully attempted to steal data from the network, but the client’s endpoint detection and response solution – Microsoft Defender for Endpoint (‘MDE’) – had intervened.
By all accounts the manufacturer’s response capabilities were mature. MDE had been installed across the majority of the systems in the environment, and a sophisticated network monitoring tool was also in place across different sites worldwide. As these tools were not flagging any untoward activity, and the account used by the threat actor to conduct the attempted data theft had been disabled, the situation appeared under control.
But, within hours the situation changed. And late on a Friday evening, the manufacturer called S-RM’s incident response team after identifying a domain administrator account downloading and installing PC Hunter. Aside from the download of a suspicious tool – PC Hunter is a favourite for ransomware groups due to its capacity to disable and tamper with antivirus software – the activity was flagged because the account in use was the same account that had attempted the data theft, and was supposed to be disabled.
For seasoned responders, this picture was immediately clear: the threat actor was still in the network and the attack was underway.
Going off (a) script
There was little time to lose. Within minutes, S-RM’s incident response team quickly identified further suspicious behaviour which matched a pattern our cyber threat intelligence experts had identified in a Cactus ransomware case just two weeks prior. While most ransomware affiliates use Group Policy Objects to deploy ransomware in a Windows-centric environment, or use internal system administration tools to do the same thing, this was different. The threat actor used a batch script to communicate with an external server – a temporary cloud hosting service called temp.sh – to download and launch their ransomware program.
What is Cyber Threat Intelligence?
- Cyber Threat Intelligence (‘CTI’) is the aggregation, enrichment and interpretation of data which provides context (capabilities, motivations and attack patterns associated with a threat), which is critical to the decision-making process.
- S-RM views CTI as an enabler for all cyber teams, facilitating the development of nuanced and actionable intelligence.
Identifying that this pattern of batch scripts and communication to temp.sh was highly likely a precursor to a ransomware attack, the team worked rapidly to intervene and stop the encryption before it began running throughout the network. Within minutes, MDE flagged an alert for the presence of Akira ransomware on a server enrolled in the program.
Stopping Akira in their tracks
With MDE already flagging the encryptor in the network, it was a matter of time before Akira successfully disabled MDE and successfully ran the ransomware across the estate. It was a complex situation: if the encryption malware began running, it would be unadvisable to stop it. Stopping ransomware when its already running can cause irreparable damage to files, and can result in being unable to recover the data even with the threat actor’s decryption tool.
Who are Akira?
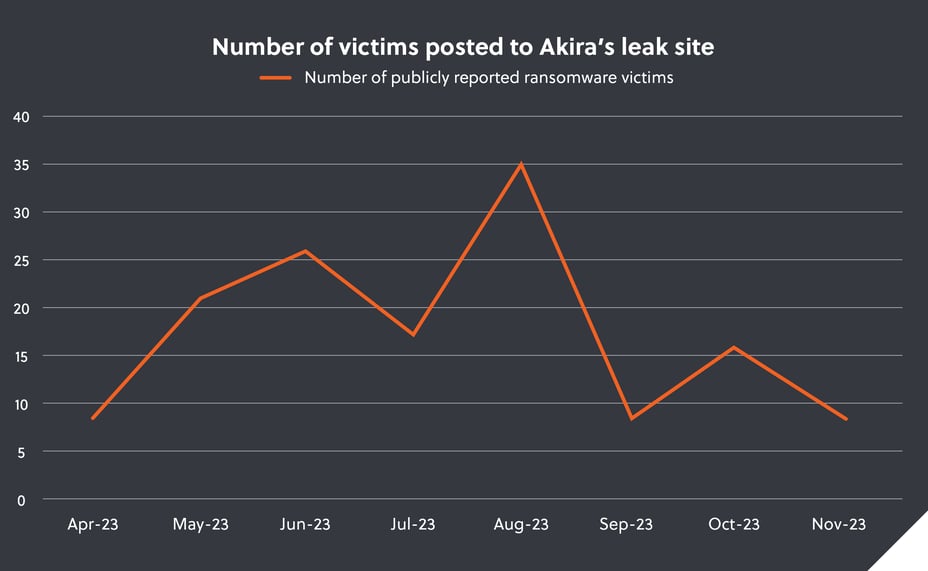
The Akira ransomware group is a sophisticated, financially motivated group, who leverages triple-extortion tactics (data exfiltration, ransomware encryption and threats to publish data until payment is made) against their victims. S-RM suspect the group, and their affiliates, are based in Russia and Commonwealth of Independent States (‘CIS’).
Instead, to slow them down, the S-RM responders immediately added the batch script, cloud hosting service, Akira ransomware binary, and other critical tools associated with the ransomware group to the client’s defensive tools. This meant that the tools did not need to manually identify the activity as malicious through its own analysis, but automatically blocked all usage at our direction. In tandem, the S-RM cyber team played a game of whack-a-mole with Akira, disabling each account they had compromised in turn, gradually limiting their access, while network containment measures aimed to limit internet connectivity to the environment.
Following hours of containment and eradication work, the response team finally removed Akira’s access to the network at 02:45 in the morning, 3 hours and 15 minutes after S-RM was asked to help. S-RM’s immediate application of threat intelligence undoubtedly changed the trajectory of the incident: In a network of thousands of servers spread across dozens of countries, Akira were able to encrypt just 1% of the devices they targeted. S-RM also prevented Akira from being able to encrypt the vital backup data, meaning the client was able to rapidly recover the impacted assets with S-RM’s technical support.
Technology is no silver bullet
The incident, and how the client responded to it, is symbolic of a broader challenge routinely faced by even the best security teams, and the best defensive technology: While high-quality tools can help organisations immediately identify and block a wide variety of malicious activity, technology cannot protect an environment on its own. As threat actors continue to successfully find ways to bypass security tools, it is critical to augment technology with cyber threat intelligence and expert technical support to meet this evolving threat.
Endpoint protection solutions are reactive tools by-design and need to see malicious activity already underway to identify it as a risk. Even when defensive technology produces an alert, it has little impact without an interpreter who can contextualise the information and identify broader behavioural patterns and how it fits with an attack chain. It is cyber threat intelligence which provides the critical context. To combat the threat posed by advanced cybercriminal groups, organisations must combine the best human expertise with the best tooling, and provide both with meaningful, actionable cyber threat intelligence.





